In this opinion article that brings us this text, I will write about the extortion system called ransomware. A type of cyber threat widely used in cryptocurrency scams. I am not really a cybersecurity expert, but I am sure I can provide some definitions and show the latest statistics on this new attack model that has been so popular in recent times, which will make these lines interesting to read.
I'll start with a brief description, as the word ransomware itself is scary, and really scary.
Un ransomware (of English Ransom, "rescue", and ware, shortening of with ), or "data kidnapping" in Spanish, is a type of harmful program that restricts access to certain parts or files of the operating system infected and at the same time it hijacks your data asking for a ransom in exchange for removing this restriction.
We are talking about a malicious software program that infects your computer. And its purpose is to display messages that demand payment of money to restore the system's functioning. This type of malware is a criminal system for making money that can be installed through deceptive links. Included in an email message, instant message or website and even with other types of external or internal attacks. Ransomware has the ability to lock a computer screen or encrypt important files with a default password.

Ransomware, an attack that is in fashion
As I indicated at the beginning of the article, ransomware It is fashionable, very fashionable and it is the extortion system called ransomware. Although attacks have become popular since the mid-2010s. But the first known attack was carried out in the late 80s by the Dr. Joseph Popp.
The creation of the creature consisted of the first documented ransomware variant in 1989, the Trojan AIDS. Curiously, the malware was distributed through the postal service using floppy disks and this use grew internationally in June 2013. The company McAfee In 2013, the US government reported that in the first quarter alone it had detected more than 250 types of ransomware unique Don't you think this is really amazing and worrying?
El Ransomware It has become so, so fashionable that it has become a service that some criminals even offer as if it were a supermarket product and I can assure you that this product is having a lot of success.
Cybercriminals have gone a step further by offering Ransomware as a Service o RaaS (of English Ransomware as a Service). And surely soon they will even be listed on the secondary or tertiary market due to the force of supply and demand. It's obviously a nice note.
The supermarket product with its barcode consists of a compact malicious kit capable of launching a malicious attack. ransomware. This kit is sold/rented to interested parties under an affiliate program to other cybercriminals who intend to launch an attack. In addition to the software, they provide them with: technical knowledge and step-by-step information on how to launch a ransomware attack using the service. As well as a platform that can even display the status of the attack using a real-time dashboard.
Sometimes, when the attack is successful, the ransom money is split between the service provider, the coder and the attacker, like good friends and it would not be otherwise. For example, the creator of the kit can collect the ransom, provide the decryption tool to the paying victims and pay 70% of the proceeds via Bitcoin to the operator. In my opinion, it really represents a new line of business based on a clear demand and when there is demand, you know…the extortion system called ransomware.
Extortion, ransomware and Bitcoin payments
Normally a ransomware It is transmitted as a Trojan or as a worm. It does this by infecting the operating system, for example, with a downloaded file or by exploiting a vulnerability. with . At this point, the ransomware will start, encrypt the user's files with a certain key. This key only the creator of the ransomware knows it, and will provoke the user to claim it in exchange for payment and normally in Bitcoin.
Once described the toy I will now go on to discuss the latest developments that have occurred in recent years, with the contribution of data, graphs and some metrics so that the importance of this new criminal phenomenon can be observed first-hand.
To start cooking this section of the article I will say that the average amount of crypto ransomware ransom has doubled since 2018.
The average ransom price for decrypting files in 2019 was reportedly $115,123. BitcoinThe average repurchase amount increased threefold and amounted to $21,700. Not bad as you can see, which encourages demand for our criminal supermarket product.
The increase in the ransom amount is explained by the fact that criminals began to attack large organizations more often and choose victims who can pay more. The maximum ransom, which is known or at least a server, was $ 5 million and was paid by a medical organization. At the same time, the extortionists demanded even more, once requesting $15 million for stolen data from a company that provides data center services and software solutions.
Let's start speeding up this article and look at some data.
In this graph we can see which sectors have shown the greatest criminal appetite.
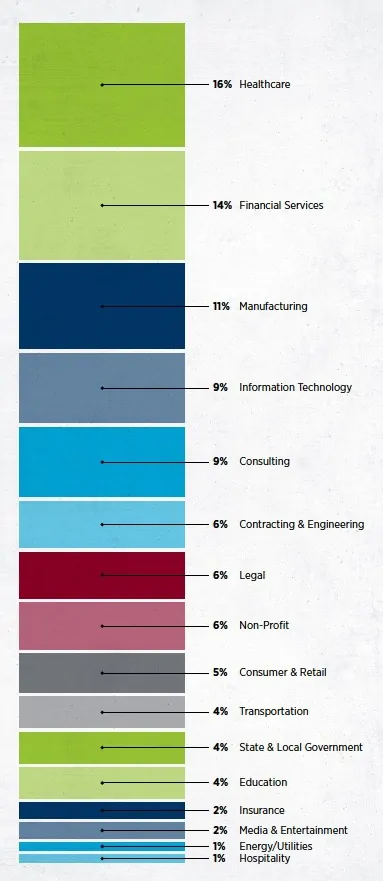
The health sector gains distinction by being the most targeted sector of 2019, accumulating a large number of Healthcare-related businesses (including healthcare organizations, healthcare device manufacturers, and technology providers). Ransomware was the attack type of choice against healthcare organizations in 2019 – they suffered more ransomware attacks than any other type and accounted for a significant 22% of all attacks analyzed globally.
Healthcare organizations were also hit hard by the attacks. BEC Business Email Compromise, representing 15% of observed incidents, as well as insider threat and inadvertent disclosure incidents (16% and 15%, respectively)
To assess another point of the graph, it should be noted that the Financial services was the second most targeted sector, accounting for 14% of security incidents. Financial services customers suffered the majority of BEC attacks; nearly 18% of all BECs globally. Financial services also fared poorly in the insider threat category at 16% and in unintentional exposure incidents at 17%, insider threat category at 18% and in unintentional exposure incidents at 20%.
It is clear that sites that mass data are very attractive and that is what I was saying, Willie Sutton when he stated that he robbed banks, because that's where the money is.
Continuing with the information, and in relation to the attack vectors, we can show this graph where we can clearly identify them.
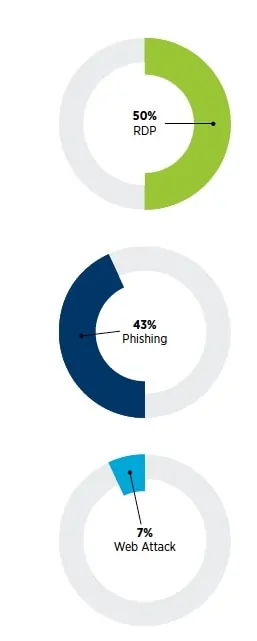
The basis of my opinion, is the act of market behavior, the initial attack vector number one was through PDR services, which RDP attacks occur in 50%. This has been a consistent trend from 2018 to the present. RDP allows users to remotely connect to other Windows-based devices or networks. It is commonly used by IT service providers or remote workers. Deploying RDP without proper controls can leave systems vulnerable. For example, weak passwords, unrestricted internet access, unlimited authentication attempts, and the use of outdated RDP protocols can leave the door open to criminal threat actors.
You may also like: Bitcoin in times of Crisis and Pandemic
The second leading attack vector for all organizations in 2019 is the social engineering. Typically referred to as phishing or spear email attack Phishing. Social engineering exploits human behavior and a criminal threatens a supermarket employee. It manipulates the victim into taking some action that allows the threat actor access to an organization's network or data. This most often occurs by inducing the victim to provide their password on a malicious website - a method known as "credential collection."
And the third attack vector is web applications. against external systems. Here, the criminal supermarket employee threatens trust by exploiting vulnerabilities in Internet applications to compromise the victim. Preventing these attacks can be difficult, as it requires extensive knowledge of all implemented frameworks and dependencies, as well as a robust vulnerability management program to keep systems up to date.
Let’s jump ahead and discover some of the variants of our criminal supermarket ransomware products, as I like to call them.
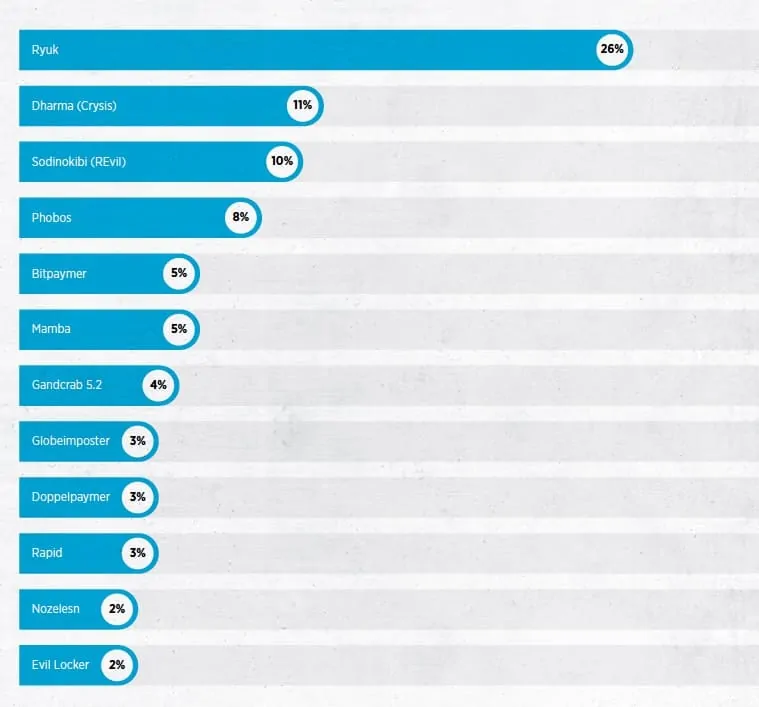
En 2017/18, malware Dharma (also called "Crysis") and SamSam were most commonly seen in all criminal investigations. Use of these variants fell in late 2018.
2019 saw the rise of ransomware variants Ryuk. Sodinokibi (also called “REvil”) and Phobos. Being really good bugs that intensified rapidly during the current year. Phobos, a variant almost identical to Dharma, entered the scene in early 2019. While Phobos is believed to have been created by the same threat group or criminal supermarket that created and ran Dharma ransomware.
Like Phobos, Sodinokibi also appeared in early 2019. Sodinokibi is widely believed to be related to GandCrab, a previously prolific ransomware variant seen in 2017 and 2018. Compared to other ransomware families, Sodinokibi is unique in that it evolved so quickly, it was the most sought-after product.
Over the course of 2019, Sodinokibi was improved several times, becoming increasingly harder to detect and more resistant to reverse engineering efforts attempting to fix it. Ryuk Ransomware, which first appeared in 2018, was the most common variant in 2019. It has been dangerously effective over the past year, in part due to the initial attack tactic used by the threat actors. From what I have been able to document, behind Ryuk is using a banking trojan called TrickBot to liberate spam / phishing effective campaigns against victims.
I'M SURE THAT MANY OF THE READERS WILL BE ASKING ABOUT THE BAILOUT MONEY, AND AS THIS IS NOT MY STYLE, I WILL NOT LEAVE THIS DOUBT UNTIL I HAVE GIVEN THE DATA IN THE FOLLOWING GRAPH.
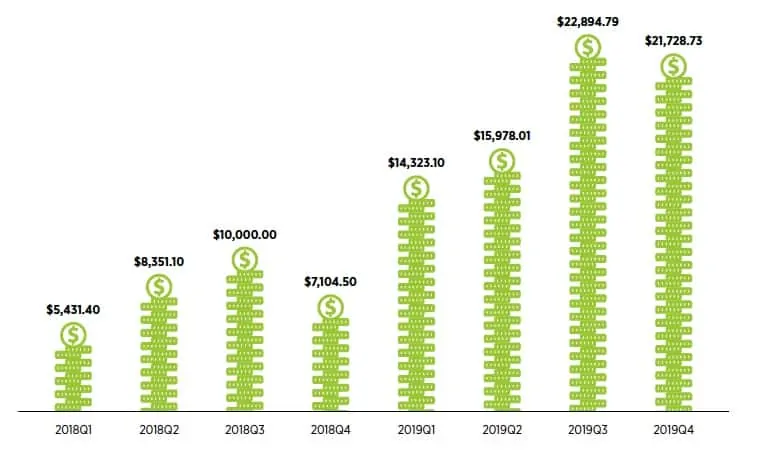
The average ransom payment has grown even more dramatically since the beginning of 2018, increasing 300% from the first quarter of 2018 to the last quarter of 2019. And that is why, as I stated earlier, it is truly an asset that represents a very good line of business, yes, a criminal business.
Hoping to have contributed my grain of sand in this criminal area, I will end the article with my opinion and a quote.
In my opinion It is an unfortunate and never-ending war that is being waged on the front lines of cyberspace. Increasingly, states and companies are much better equipped and trained for battle. However, many of those who can fight directly in this war are forced to take up arms in order to take measures that will make them stand on their own two feet.
While this war is invisible to most and fought in the realms of the vast and indefensible internet, the costs are tangible and truly astronomical: Cybercrime is everyone's problem and a risk for all businesses, a sinister spectre that cannot be completely subdued. And that is why we must educate ourselves and occupy educational spaces like the one we offer in Academy to understand and reduce risks.
Y I conclude with the announced quote from a renowned cybercrime soldier.

Cybercrime isn’t going away anytime soon. It’s not a war with a defined end – it’s a continuous, rigorous routine that requires diligence, attention and experience. Suit up, dig in and keep fighting. By the general Michael Hayden, a retired four-star United States Air Force General, the former director of the Central Intelligence Agency (CIA), and former director of the National Security Agency (NSA) Undoubtedly a leading and recognized expert in security, intelligence, global terror and cyber risks.
Continue reading: Erebus, an attack that can censor Bitcoin



