
Hackers take advantage of a bug in Bitcoin ATMs to divert all incoming funds.
On August 18, the manufacturer of Bitcoin ATMs, General Bytes, suffered a zero-day attack, which allowed hackers to become administrators by default and modify ATM settings so that all incoming funds were automatically transferred to their wallet addresses.
For the moment, The amount of stolen funds and the number of Bitcoin ATMs that have been compromised have not been revealed., but the company has advised operators to update the ATM software urgently, in order to solve the vulnerability.
The company, which has more than 8.800 Bitcoin ATMs and operates in 120 countries, has also asked the users to refrain from using ATMs until they update their server to versions 20220725.22, and 20220531.38 for clients running 20220531.
They have also advised customers to modify your server's firewall settings so that the CAS management interface can only be accessed from authorized IP addresses, among other things.
Finally, the company has warned customers that they should review your “SELL Crypto Setting” to ensure that the hackers have not made changes to the settings so that the funds received are transferred to them and not to the clients.
General Bytes has also noted that perform regular security audits of their Bitcoin ATMs since their creation in 2020 and that they had not found this type of vulnerability in any of them.
How did the attack on Bitcoin ATMs occur?
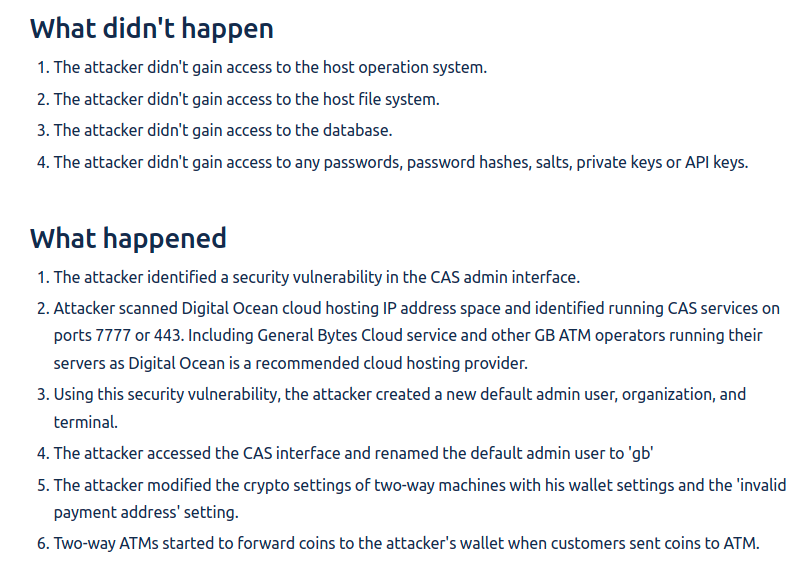
General Bytes published an article analyzing the attack. In it, they have indicated that the hackers carried out a zero-day vulnerability attack to access the company's cryptocurrency application server (CAS) and withdraw the funds.
The CAS server manages the entire operation of the ATM, which includes the purchase and sale execution of crypto on exchanges and what currencies are supported.
General Bytes believes the hackers scanned for exposed servers running on the TCP ports 7777 or 443, including servers hosted on General Bytes' own cloud service.
In this way, hackers added themselves as an administrator by default in the CAS and proceeded to modify the buy and sell settings in such a way that any crypto received by the Bitcoin ATM would instead be transferred to the hackers' wallet address.
[hubspot type=cta portal=20298209 id=38fb28e1-1dc1-40e3-9098-5704ca7fcb07]



