
The rise of cryptocurrencies has attracted the interest of investors and also of hackers, who are becoming more ingenious every day in their complex attacks on legitimate users and companies in the crypto industry.
Microsoft security threat intelligence researchers have discovered a new attack pattern, identified as DEV-0139, that targets businesses and cryptocurrency users.
In its blog, the technology company detailed that DEV-0139 exploits Telegram groups, which are used by cryptocurrency companies to communicate and interact with their customers, to expand and target their goals.
According to Microsoft researchers, DEV-0139 is one of the most complex attacks ever seen in the industry, revealing a great deal of knowledge and preparation on the part of hackers, who are willing to gain the trust of their victims before stealing their crypto assets.
DEV-0139 How does it affect cryptocurrency users and businesses?
DEV-0139 acts in a sophisticated and stealthy manner, taking steps to gain the trust of victims before initiating the attack.
As detailed by Microsoft, the DEV-0139 threat actor leveraged the Telegram groups of certain cryptocurrency startups, posing as representatives or employees of another crypto company, such as OKX. In the Telegram groups using fake profiles, the threat actor pretended to ask for feedback on the fee structure used by cryptocurrency companies, inviting members of the targeted group to join a different group within the messaging platform.
After gaining the trust of victims, Microsoft explains, the DEV-0139 threat actor sent an Excel attachment to victims, named “OKX Binance & Huobi VIP fee comparison.xls” which contained several tables on fee structures between cryptocurrency exchange companies.
Researchers say the data presented in the file was probably quite accurate in order to increase credibility and fool victims. But that's where the real threat begins.
Downloading the Excel file sent by the threat actor triggers a series of activities aimed at infiltrating the systems and accessing victims' data to ultimately steal their cryptocurrencies.
The DEV-0139 attack
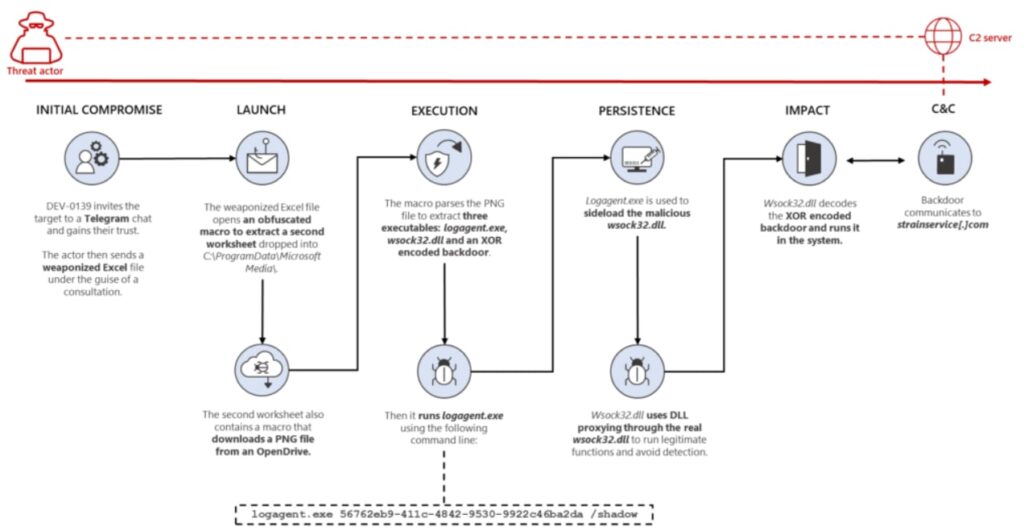
First, the Excel file launched a macro or action that misused the UserForm interface to create a user form in order to obfuscate the malicious code and obtain some data from potential victims.
After this, the macro released another Excel spreadsheet embedded in the user form, which was executed in invisible mode. This second spreadsheet was base64 encoded and downloaded to the address C:\ProgramData\Microsoft Media\, with the name “VSDB688.tmp”.
The “VSDB688.tmp” file downloaded another PNG file containing three more executable files: the first was a legitimate Windows file called “logagent.exe”; the second was a malicious version of the dynamic link library (DLL) called “wsock32.dll”; and finally, the third file was an XOR-encoded backdoor.
Source: Microsoft
The XOR-encoded backdoor allowed the DEV-0139 threat actor to remotely access the infected system of their victims, making it easier for the attacker to collect victim data in order to fraudulently access and appropriate their cryptocurrency.
The attack described by Microsoft began in a Telegram group on October 19 of this year.
Is Lazarus Group Behind This Attack?
In addition to the DEV-0139 threat actor, Microsoft researchers analyzed another similar attack, which used a file under the same DLL proxy technique, implying that the same threat actor is running other malicious campaigns using these attack techniques.
On the other hand, Volexity has linked the threat actor DEV-0139, identified by Microsoft, as the same one that executed a campaign targeting cryptocurrency users with a variant of the AppleJeus malware, through malicious Microsoft Office documents. This threat actor was identified by Volexity as the North Korean hacker group, Lazarus Group.
Continue reading: Bit2Me achieves ISO 27001 accreditation in its commitment to excellence in cybersecurity



